The Darkish Internet: Exploring the Hidden Web

Within the realm of the Web, few issues carry as notorious a fame because the Darkish Internet. Broadly utilized for cybercrime, theft, cash laundering, terrorism, and human abuse, it stays the goal of numerous authorities and businesses, all vying to catch its prison customers and curb its utilization. Paradoxically, the very basis of the Darkish Internet was developed by the US navy and made accessible to the general public, freed from cost.
Welcome to the Darkish Internet – a really seedy and sinister nook of the net, or might it even be a device for freedom and civil rights? Let’s discover out…
TL;DR: What’s the Darkish Internet?
The Darkish Internet is a community of internet sites that function on an encrypted layer of the web, inaccessible to straightforward net browsers. It is predominantly accessed by way of Tor or I2P. These networks anonymize consumer information by routing it by a number of servers worldwide, encrypting it at every stage (referred to as ‘onion routing’). This makes each the origin and content material of the information troublesome to hint.
Web sites on the Darkish Internet use “.onion” or “.i2p” top-level domains and are usually not listed by normal search engines like google, offering an setting of elevated privateness and anonymity.
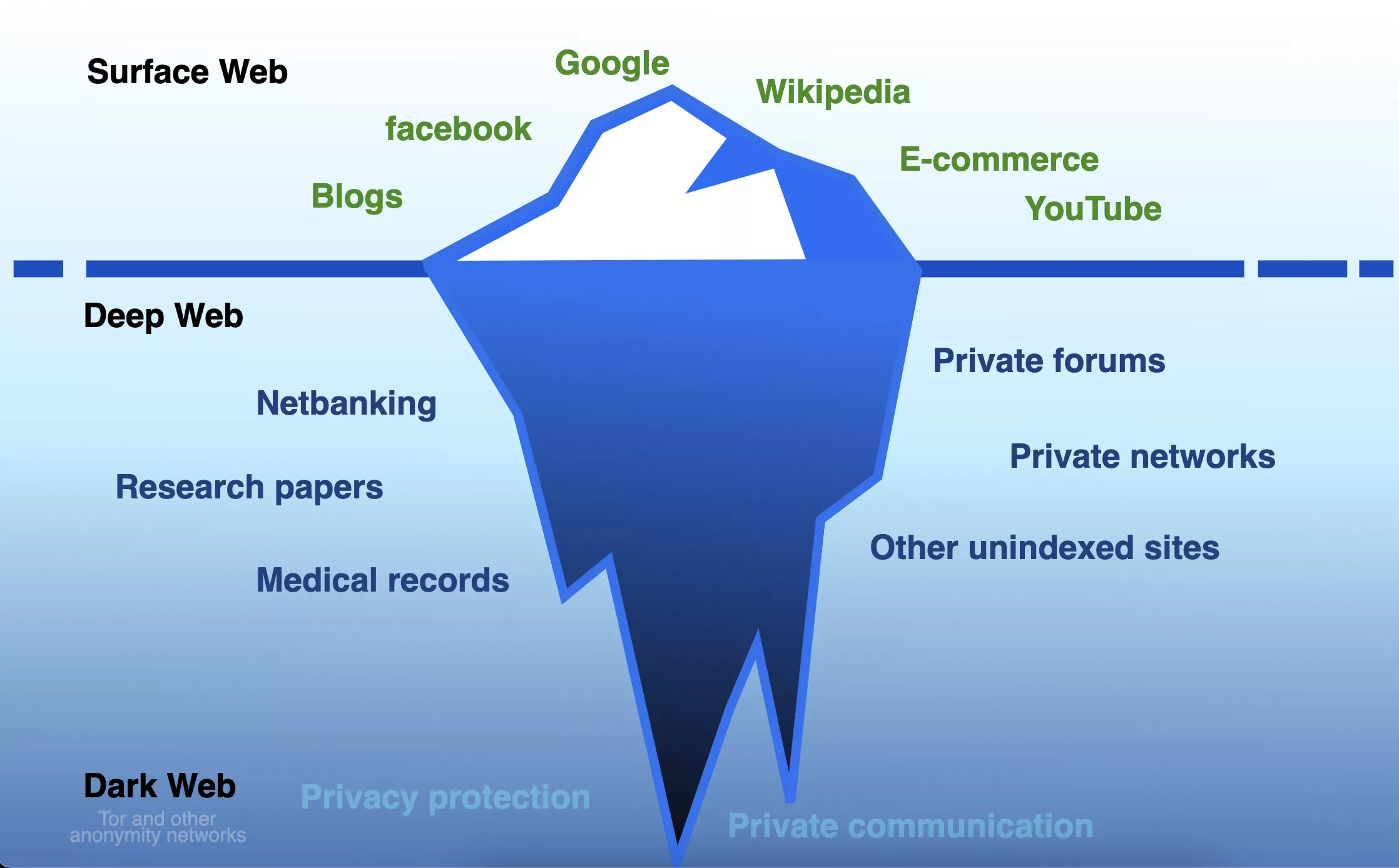
Floor net, deep net, and darkish net
The Web is a worldwide community of computer systems as you are possible already conscious. Among the many many information programs using this community is the World Huge Internet (WWW). Once you use an online browser to go to a web site like TechSpot, your pc is requesting recordsdata hosted on a distant machine, some other place on the planet.
A mess of machines seamlessly deal with this course of for you – connecting you to the suitable server, transferring the recordsdata your browser requests, and so forth. You possibly can find any of our net pages, together with billions of others, as a result of they’re publicly accessible and have been listed by the likes of Google.
This accessible phase of the net is broadly known as the Surface Web, but it constitutes only a small fraction of the whole information accessible by the Web. The rest, which is not listed, is commonly termed the Deep Web.
Deep Internet information is comparatively hidden, however not invisible – for instance, cloud storage and on-line banking companies, in addition to web-based e-mail, authorities, and different businesses are all positioned inside the Deep Internet. If you recognize the precise location of it, by way of its URL or IP deal with, then you’ll be able to simply get to it, although it is more likely to be saved safe with passwords or some form of fee system.
This type of content material is not listed as a result of the computer systems that host the information block automated packages, referred to as bots, from trawling by the websites, as a part of the indexing course of. It does not essentially imply the computer systems comprise something unlawful or are getting used for something nefarious (they’re, in any case, completely seen on the Web) – it is merely a matter of improved safety and privateness.
Nonetheless, there are Web customers who take these privateness measures to an excessive degree, using a extremely non-public community of computer systems that may solely be accessed utilizing the suitable software program. Furthermore, the areas and login credentials are unique information to particular people.
The content material hosted on these machines is collectively known as the Darkish Internet.
Darknets: hiding in plain sight
Because the Floor Internet is so accessible, as is almost all of the Deep Internet if you recognize the place to look, you is likely to be questioning how precisely one can utterly cover a group of servers that in the end nonetheless connects to the Web.
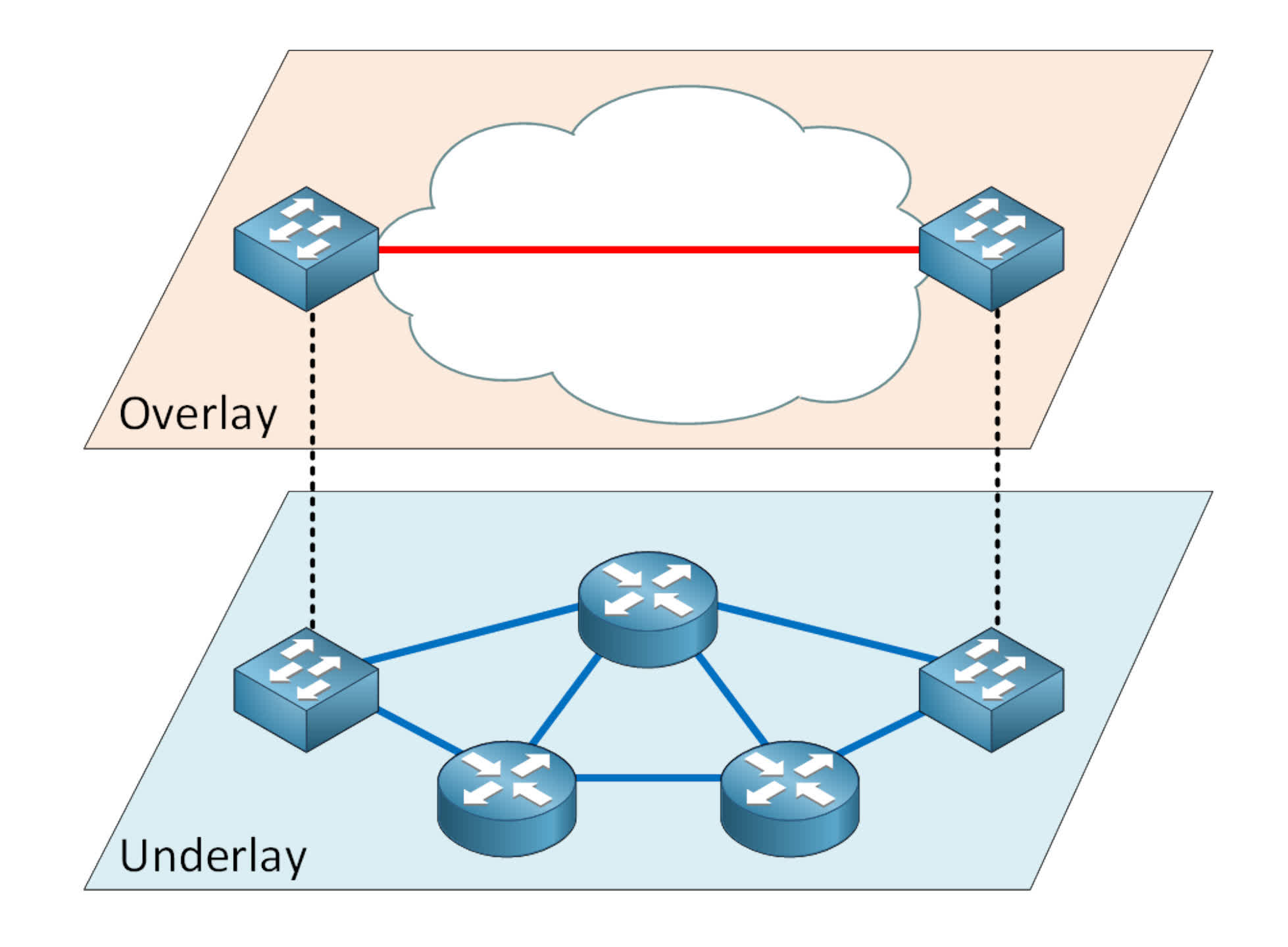
It is achieved by way of overlay networks (teams of computer systems that use one other community to speak by) that may solely be accessed by the usage of particular software program, networking protocols, or unique authorization.
Particular variations of those programs are sometimes labeled as darknets and are used to do issues like peer-to-peer file sharing. Nonetheless, the usage of a darknet itself doesn’t suggest that all the things is hidden – accessing one from your house ISP account will depart an identifiable hint again to you.
The Darkish Internet contains a mess of darknets which might be employed to host so-called nameless proxy networks – these use a number of servers appearing as relays, transferring information from machine to machine, and encrypting the transactions as they arrive and go. The extra relays used, the more durable it turns into to trace all the things inside the darknet.
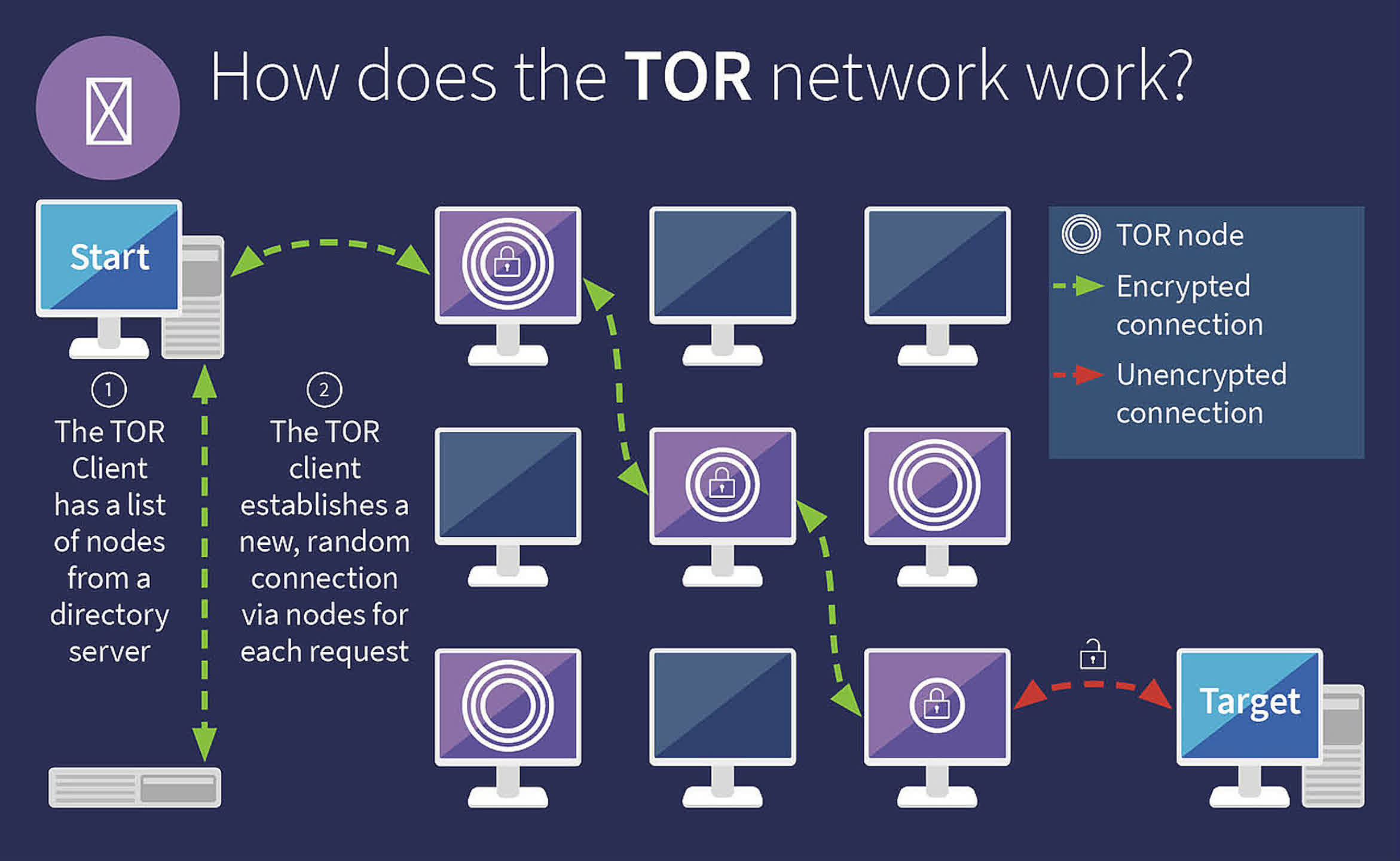
One of the crucial well-known programs that do that is known as Tor and it is named after the expertise itself: The Onion Router. Onion routing was initially developed by the US Naval Analysis Laboratory within the mid-Nineties, as a method to guard intelligence transmissions throughout the Web, by the usage of a number of encryption layers (therefore ‘onion’). The code was finally launched beneath a free license and shortly a lot of initiatives began showing based mostly on it (Tor simply being one in every of them).
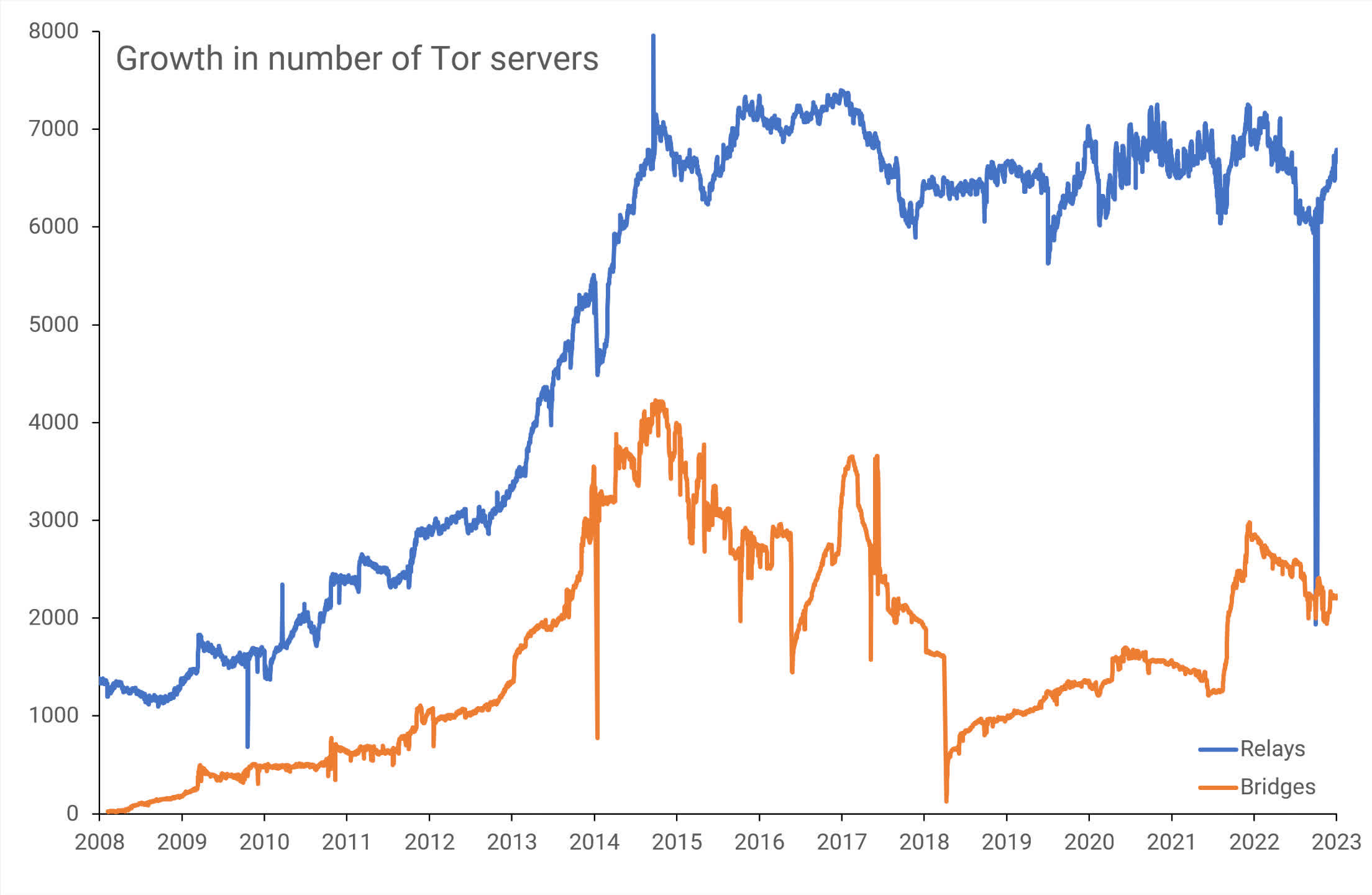
Servers in Tor’s darknet are owned and run by volunteers, and at present quantity within the 1000’s, all throughout the globe. Some are publicly listed (relays), whereas others aren’t (bridges), and get utilized by millions of people every single day.
What the Darkish Internet is used for
The very first thing to notice right here is that accessing content material positioned inside the Darkish Internet is not unlawful, in most international locations at the least – the exceptions being people who monitor and closely police all on-line actions, no matter what a part of the Internet it is in.
Having a really safe and personal community, which actively tries to maintain its customers as hidden as doable, goes to be of use to quite a few authorities our bodies, in addition to people needing safety, equivalent to political dissidents and whistleblowers, or just simply customers who want to preserve their digital content material as non-public and protected as doable.
In international locations the place merely expressing an open view essential of governing insurance policies, might result in arrest and much worse, the usage of darknets affords one of many few technique of safely speaking with others. It does imply, although, that conspiracy obsessives, these far past the likes posting wild concepts on social media, are additionally frequent customers of those hidden networks, normally from being repeatedly banned from public web sites within the Floor Internet.
And the very nature of the Darkish Internet additionally makes it best for these wishing to hold out unlawful actions or retailer content material that is way more critical and unlawful in all components of the world.
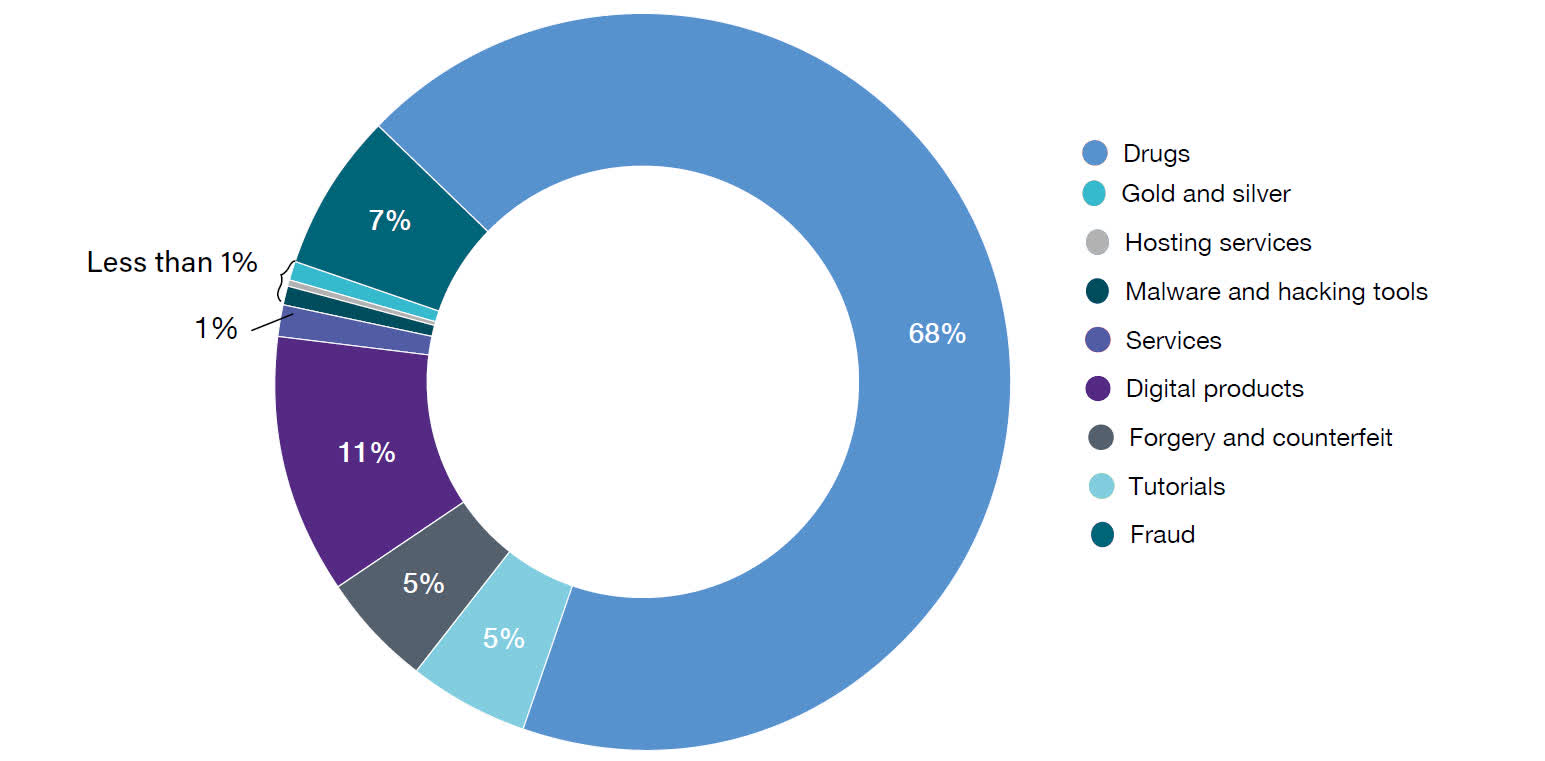
Knowledge that has been stolen, counterfeit cash, solid paperwork, bank card and social safety numbers are all typically sold by folks frequenting the Darkish Internet. Websites promoting low cost prescribed drugs sit side-by-side with these providing firearms, narcotics, or pornographic materials involving minors.
Lately, affords of cybercrime services have risen in quantity, as ransomware attacks have focused ever-larger corporations, and hacking teams routinely use darknets to debate targets, share software program, and so forth (although sometimes to the good thing about the legislation).
It’s these that give the Darkish Internet its fame and it isn’t laborious to see why.
Accessing the Darkish Internet
It is value noting that one can’t merely stumble throughout any of the above, just by logging on to your house Web account and utilizing an everyday net browser. Within the case of the latter, one thing just like the Tor Browser is required to entry content material inside the Darkish Internet.
This program can be utilized similar to some other browser, however its “hidden companies” options enable customers to entry the entire Internet, with out revealing their location or different figuring out traits. It is utilized by 1000’s of individuals, every single day, for completely smart and bonafide causes.
Tor is not a VPN (Virtual Private Network) nevertheless it does use multi-layered encryption for all information transferred in searching periods and might entry the Tor Community, which different browsers cannot do. This can be a assortment of 1000’s of servers, throughout the globe, maintained by nameless volunteers. Simply because the servers that host TechSpot are a tiny a part of the Floor Internet, the Tor Community is a small a part of the Darkish Internet.
Now, whereas some authorities use Tor themselves for managing the switch of covert info, many others view anybody who makes use of this system with deep suspicion. And given the character of some (many?) of the customers of the Darkish Internet, any try to make use of the Tor Community needs to be achieved fastidiously – so which means taking your on-line privateness and safety as significantly as doable.
One method is to make use of an previous pc, that is not your most important machine, and run it with one thing just like the Tails operating system. This moveable Linux distribution is designed to run straight off a USB flash drive and comes with Tor pre-installed. In different phrases, you boot the pc utilizing Tails, moderately than Home windows, for instance.
Subsequent, if you wish to ramp up your privateness additional, do not use your house ISP. As an alternative, connect with a public WiFi hotspot however as these aren’t very safe, utilizing a VPN earlier than firing up Tor is an absolute should.
It is considerably apparent to say this, nevertheless it’s nonetheless value repeating – do not use your personal title or e-mail deal with. Randomized, throwaway accounts are very important for making certain you are not leaving a path again to your private particulars. And whereas GB of free recordsdata might sound attractive, there is a good probability that they are merely carriers for malware, so do not obtain something until you are 100% sure of the file’s integrity and origins.
Sensible (and authorized) makes use of for the Darkish Internet
As famous, though the Darkish Internet could be a place for illicit actions, you might also leverage it in accountable and moral makes use of, in compliance with native legal guidelines and laws.
- Privateness-focused Electronic mail Companies:
- ProtonMail, a Swiss-based e-mail service, is accessible on the Darkish Internet to keep away from censorship and supply an encrypted e-mail service. It is best for these wanting to speak confidentially.
- Whistleblowing:
- Platforms like SecureDrop enable nameless information-sharing, and it is utilized by journalistic entities together with The Guardian and The New York Instances for safe communication with whistleblowers.
- Fb:
- Facebook has a presence on the Darkish Internet, letting folks entry the platform from areas the place it is blocked or censored. It is helpful for folks residing beneath oppressive regimes. DuckDuckGo can also be out there within the Darkish Internet as a tracker-free search engine.
- Privateness and Freedom Advocacy:
- The Tor Project makes use of the Darkish Internet for its web site to offer details about web privateness, safety, and freedom from surveillance.
- Cryptocurrency Transactions:
- Bitcoin and different cryptocurrencies may be transacted over the Darkish Internet, offering an additional layer of anonymity to customers. This may be helpful for folks residing in international locations with strict monetary controls.
- Web Freedom in Oppressive Regimes:
- For folks in international locations with strict web censorship, the Darkish Internet could be a lifeline, offering entry to uncensored information and the power to speak freely with the skin world. Websites such because the BBC and ProPublica can be found within the Darkish Internet.
A cautionary notice to finish with
For some folks on the planet, utilizing the Tor Community or comparable networks is the one means they will safely entry the Web, with out speedy reprisals from oppressive regimes. With out the existence of the Darkish Internet, most people would have much less information in regards to the machinations of governments and companies or crimes dedicated in conflicts.
However for all of the optimistic points of the Darkish Internet, the title is now ever related to critical crime, within the eyes of most governments. With the worldwide value of cybercrime estimated by some to succeed in $10 trillion in just some years, and large-scale businesses heavily focusing on combating the usage of the Darkish Internet, even probably the most respectable customers could discover themselves being focused.
So by all means, obtain Tor and discover the hidden world of the Darkish Internet, however simply bear in mind who else makes use of it and why.
Masthead credit score: Robynne Hu