Zero-click iOS exploit has been infecting iPhones with ‘Triangulation’ spyware and adware since 2019

Why it issues: Apple has been extolling the safety structure of iOS for years, however the locked-down nature makes it onerous for safety researchers to examine the working system and detect indicators of a cyberattack. That is why even a revered safety agency like Kaspersky can spend years in the dead of night a few spyware and adware marketing campaign focusing on its company units.
Russian cybersecurity agency Kaspersky says it has discovered an “extraordinarily complicated” assault that impacts all iPhones operating iOS 15.7 or older variations however appears to be primarily aimed toward iOS units owned by Kaspersky administration and key staff.
The timing of the report coincides with public allegations thrown by Russian intelligence at its US counterpart. The Kremlin’s Federal Safety Service (FSB) claims that Apple has been working intently with the Nationwide Safety Company (NSA), offering the latter group with a backdoor in order that it may plant spyware and adware on 1000’s of iPhones belonging to diplomats of Russia, NATO members, Israel, China, and a few ex-Soviet nations.

Kaspersky is conscious of the FSB claims however has been unable to confirm if there is a hyperlink between the 2 assaults. The corporate explains that whereas the spyware and adware described by the FSB seems to be just like the one it discovered on telephones belonging to its prime and middle-management, the Russian company has but to supply a technical evaluation of the malware in query.
As for Apple, the corporate refused to touch upon the accusations however wished to notice that “now we have by no means labored with any authorities to insert a backdoor into any Apple product and by no means will.”
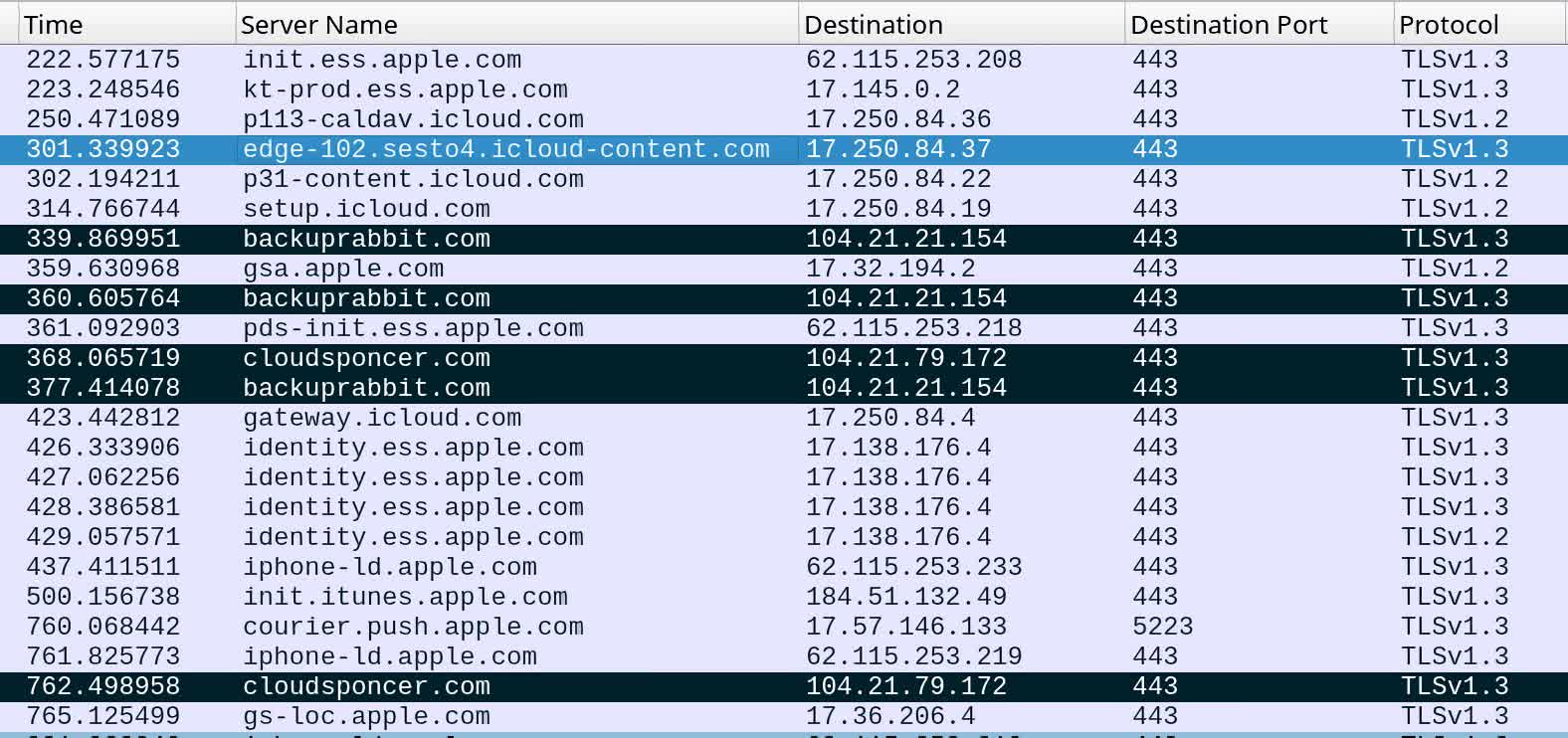
Circling again to the pressure of spyware and adware noticed by Kaspersky, it seems to be like one more instance of a zero-click attack. The researchers dubbed it Triangulation to focus on that it is a part of a stealthy intrusion marketing campaign that makes use of Canvas fingerprinting to depart a yellow triangle within the goal units’ reminiscence. After analyzing its personal company community visitors, the corporate discovered the marketing campaign continues to be ongoing and will have been energetic since 2019.
The assault chain begins with attackers sending victims a specially-crafted message by way of Apple’s iMessage service. As soon as obtained, a malicious attachment within the message mechanically begins the exploit with out the individual in query opening the message or the attachment. Earlier than the sufferer has an opportunity to delete the message, the malicious code executed via the exploit may have already downloaded the spyware and adware that offers hackers deeper entry to the goal machine.
Kaspersky researchers have been in a position to analyze the contaminated units by recovering information from backups made utilizing the Cell Verification Toolkit. Additionally they observe the malware they found won’t persist on the machine after a reboot, although they’ve seen proof of reinfection for a number of the affected telephones.
As of writing, it is unclear what vulnerabilities are used within the assault chain. Nonetheless, Kaspersky believes one of many flaws is a kernel extension flaw tracked beneath CVE-2022-46690 that Apple patched in December 2022 with the discharge of iOS/iPadOS 16.2. On the time, the Cupertino firm additionally began distributing iOS 15.7.2 to older units with fixes for a number of high-risk, “actively-exploited” vulnerabilities.
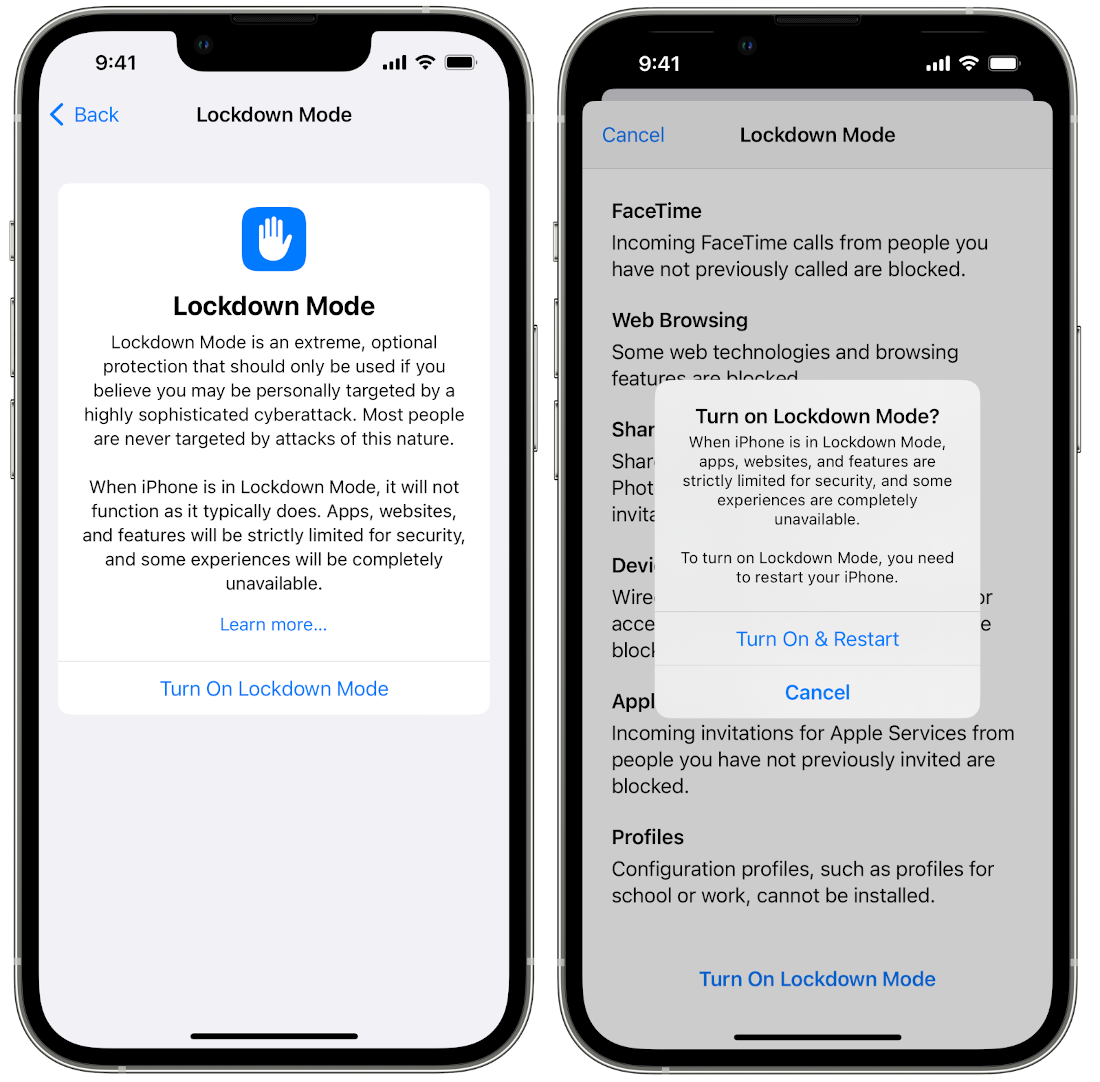
It is also price noting that individuals who consider they’re vulnerable to highly-targeted cyberattacks can use an excessive safety measure referred to as Lockdown Mode. That is an non-compulsory characteristic that Apple launched with iOS 16 macOS Ventura which drastically limits the assault floor for hackers, with the trade-off being that apps, web sites, and OS-level options will not work as anticipated.
Picture credit score: Ameen Almayuf, Maarten Dirkse