Vulnerabilities lead to hundreds of thousands of compromised customers of common managed file switch software program

[ad_1]
In context: Progress Software program’s enterprise-level managed file switch utility, Moveit, has had a foul month. Lower than just a few weeks in the past, recognized Russian-linked menace actors and ransomware teams actively exploited two vulnerabilities, impacting personal, company, and authorities clients.
Progress Software program’s newest concern, tracked as CVE-2023-35708, is a SQL injection vulnerability that hackers can exploit to realize escalated privileges and unauthorized entry to Moveit’s database. On this case, attackers can submit a crafted payload to a Moveit Switch utility endpoint, offering them with unauthorized entry to its database content material.
The brand new safety gap joins two comparable, beforehand reported points, CVE-2023-34362 and CVE-2023-35036. Based on Progress Software program’s advisory, any variations launched earlier than 2021.0.8 (13.0.8), 2021.1.6 (13.1.6), 2022.0.6 (14.0.6), 2022.1.7 (14.1.7), 2023.0.3 (15.0.3) are in danger.
ICYMI: @CISAgov & @FBI are working carefully to handle dangers posed by the #MOVEit vulnerability & urge orgs to use mitigations detailed in our joint advisory: https://t.co/4sCMsJ4mj9. Any org observing uncommon exercise ought to instantly notify CISA or FBI so we will help. pic.twitter.com/Exs4W4eeWs
– Jen Easterlyð¡ï¸Â (@CISAJen) June 16, 2023
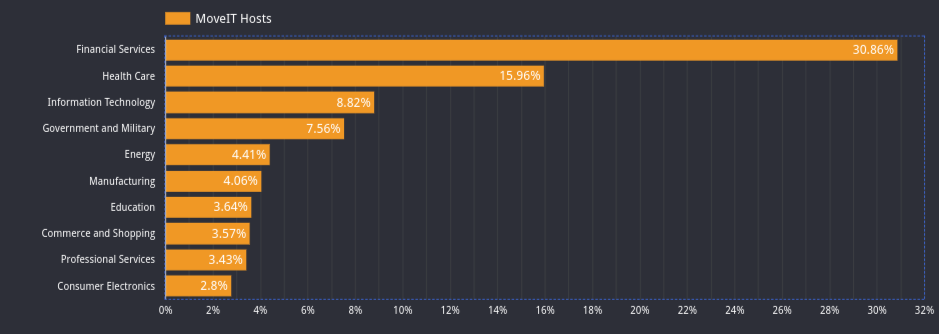
The variety of present Moveit hosts and customers is way from insignificant. Based on a report from censys.io, greater than 3,000 hosts are working the managed file switch answer. Greater than 30 p.c of the hosts working the software program are within the monetary companies trade. Greater than 15 p.c of consumers are from the healthcare trade, nearly 9 p.c work in data expertise, and over 7.5 p.c are from authorities and navy installations. Twenty-nine p.c of the organizations noticed within the report make use of greater than 10,000 people.
Progress Software program recommends that customers and hosts patch the product and mitigate the vulnerabilities instantly. The announcement supplies a number of remediation paths for customers and directors to make sure they’re now not prone to the recognized exploits. Customers who haven’t utilized the Might 2023 patch ought to observe the mitigation steps within the Moveit Switch Important Vulnerability article. That web page accommodates the newest patches, together with the repair for the June 9 (CVE-2023-35036) vulnerability and the unique vulnerability from Might 31 (CVE-2023-34362). As soon as full, proceed to the Fast Mitigation Steps and apply the June 15 patch as outlined. You’ll then be updated for the vulnerabilities introduced on Might 31, June 9, and June 15.
Researchers imagine the Clop ransomware gang has been conscious of the vulnerability since 2021. Based on Cybersecurity and Infrastructure Safety Company Director Jen Easterly, the assaults have up to now primarily been opportunistic and had no vital impression on federal civilian businesses. Easterly additionally stated, “…we aren’t conscious of Clop actors threatening to extort or launch any information stolen from U.S. authorities businesses.”
Picture credit score: censys.io
[ad_2]
Source