Outstanding cryptocurrency trade contaminated with beforehand unseen Mac malware

[ad_1]

Getty Photographs
Researchers have found beforehand unknown Mac malware infecting a cryptocurrency trade. It accommodates a full suite of capabilities, together with the flexibility to steal non-public knowledge and obtain and execute new malicious information.
Dubbed JokerSpy, the malware is written within the Python programming language and makes use of an open supply instrument generally known as SwiftBelt, which is designed for authentic safety professionals to check their networks for vulnerabilities. JokerSpy first got here to mild earlier this month in this post from the safety agency Bitdefender. Researchers for the corporate stated they recognized Home windows and Linux elements, suggesting that variations exist for these platforms as effectively.
5 days later, researchers for safety agency Elastic reported that the diagnostic endpoint safety instrument they promote had detected xcc, a binary file that’s a part of JokerSpy. Elastic didn’t determine the sufferer aside from to say it was a “outstanding Japanese cryptocurrency trade.”
As soon as xcc executed, the unknown risk actor tried to bypass so-called TCC protections in macOS that require specific permission from a person earlier than an app can entry a Mac’s exhausting drive, contacts, and different delicate sources or document its display screen.
By changing the prevailing TCC database with their very own, the risk actors have been possible attempting to suppress alerts that will in any other case seem when JokerSpy runs. In previous assaults, risk actors have been in a position to bypass TCC protections by exploiting vulnerabilities in them. Researchers have additionally demonstrated attacks that have been in a position to do the identical factor.
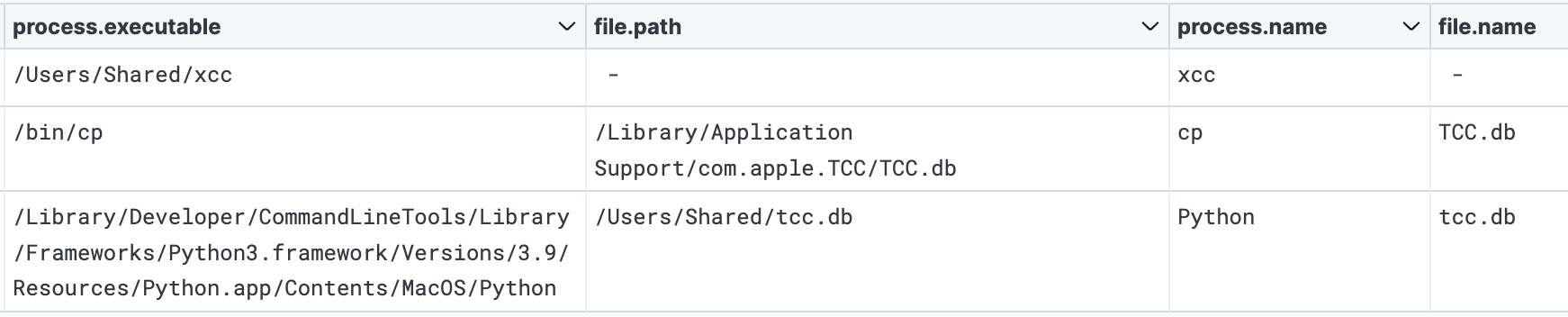
Menace actor creating/modifying and shifting a TCC database, after which executing xcc.
Elastic
The xcc executable checks the TCC permissions and identifies the app the person is presently interacting with. It then downloads and installs sh.py, the primary engine for the JokerSpy malware. It accommodates the standard backdoor capabilities, together with:
| Command | Description |
|---|---|
| sk | Cease the backdoor’s execution |
| l | Checklist the information of the trail supplied as parameter |
| c | Execute and return the output of a shell command |
| cd | Change listing and return the brand new path |
| xs | Execute a Python code given as a parameter within the present context |
| xsi | Decode a Base64-encoded Python code given as a parameter, compile it, then execute it |
| r | Take away a file or listing from the system |
| e | Execute a file from the system with or with out parameter |
| u | Add a file to the contaminated system |
| d | Obtain a file from the contaminated system |
| g | Get the present malware’s configuration saved within the configuration file |
| w | Override the malware’s configuration file with new values |
“As soon as a system is compromised and contaminated with malware like JokerSpy, the attacker successfully has a fantastic diploma of management over the system,” researchers with macOS safety agency Intego wrote on Friday. “With a backdoor, attackers can set up extra elements within the background and will probably run additional exploits, monitor customers’ conduct, steal login credentials or cryptocurrency wallets, and extra.”
Researchers nonetheless aren’t positive how JokerSpy will get put in. Elastic researchers stated they “strongly imagine that the preliminary entry for this malware was a malicious or backdoored plugin or third celebration dependency that supplied the risk actor entry.” This principle aligns with observations from researchers at Bitdefender who correlated a hardcoded area present in a model of the sh.py backdoor to a series of tweets about an contaminated macOS QR code reader that was discovered to have a malicious dependency. Elastic additionally stated the risk actor it noticed already had “present entry” to the Japanese cryptocurrency trade.
The posts linked above checklist numerous indicators that folks can use to find out in the event that they’ve been focused with JokerSpy. Moreover cryptographic hashes of assorted samples of xcc and sh.py, indicators embody contact with domains at git-hub[.]me and app.influmarket[.]org. Whereas JokerSpy went undetected by the overwhelming majority of antivirus engines when the malware first got here to mild, a a lot wider physique of engines is ready to determine it now. Whereas there is no such thing as a affirmation that Home windows or Linux variations of JokerSpy exist, individuals ought to be conscious that’s a definite risk.
[ad_2]
Source



