Malvertising assault makes use of Punycode character to unfold malware via a faux “KeePass” web site

Facepalm: Punycode is an encoding method designed to symbolize Unicode characters throughout the less complicated ASCII character set. When used at the side of internet addresses, Punycode characters present cybercriminals with a robust technique to focus on new victims amongst unsuspecting web customers.
Punycode-enhanced methods for spreading malware and cyber-attacks have been recognized since 2017 when an online developer created a proof-of-concept website that resembled apple.com. Punycodes stay extremely efficient immediately, particularly when employed in a malicious promoting marketing campaign that intently mimics authentic web sites.
In line with Malwarebytes Labs, a current marketing campaign focused the KeePass web site utilizing a malicious advert hosted on Google. Customers had been deceived with a faux internet web page impersonating the official website of the open-source password supervisor, KeePass. This marketing campaign exploited a Punycode character to create a convincing imitation of the actual webpage.
Malwarebytes analysts reported that the malicious advert was served in response to look queries for “keepass.” It was notably misleading as a result of it displayed the official KeePass brand and URL, showing earlier than natural search outcomes. This misleading look made it practically indistinguishable from the authentic website. When customers clicked on the advert, they had been redirected to a seemingly safe (HTTPS) internet web page designed to imitate the official KeePass web site.
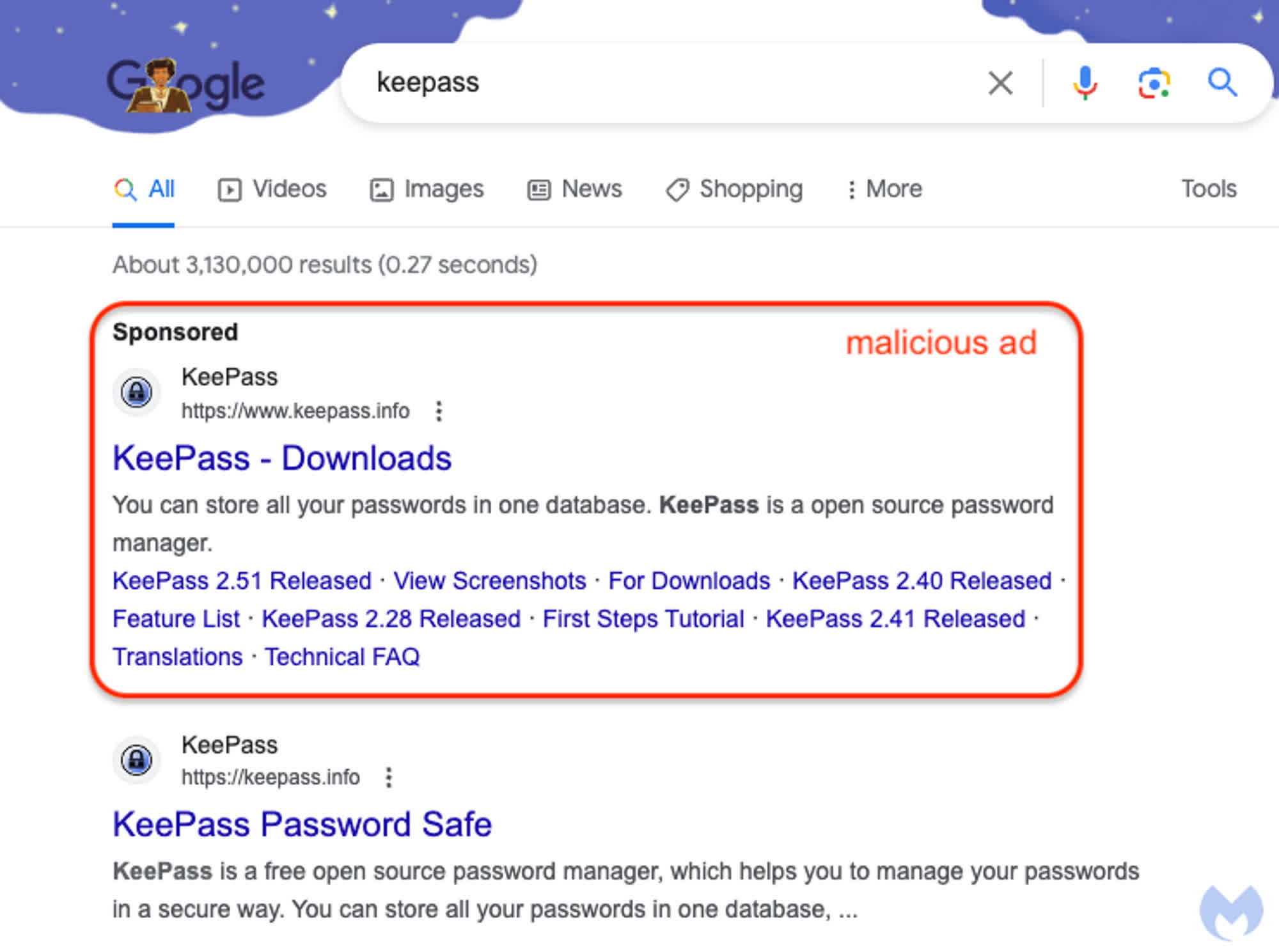
Malwarebytes found that the faux web site was utilizing Punycode to interchange the preliminary “okay” within the area identify. Whereas Punycode is subtly employed, it successfully disguises the malicious nature of the actual web site, which is represented as “xn--eepass-vbb” dot information.
This fraudulent website provides a malicious .msix installer rather than the official KeePass obtain, which comprises a PowerShell script related to the FakeBat malware household. This script is meant to hook up with a command and management server run by cybercriminals, enabling them to obtain a brand new malware payload onto the compromised system.
Menace actors have been utilizing Punycode characters with internationalized domains in phishing campaigns for years, as famous by Malwarebytes. The current case involving KeePass demonstrates the continued effectiveness of this system, notably when mixed with model impersonation campaigns carried out via malicious advertisements hosted by Google. To mitigate the menace, customers can manually enter the official URL of their browser or keep away from clicking on “sponsored” messages displayed earlier than real search engine outcomes when searching for software program downloads.



