Hackers are utilizing Punycode to create authentic-looking URLs in Google adverts

In context: Google’s search adverts are already misleading sufficient. Positive, they’re marked with a “sponsored” indicator, however they nonetheless seem as a legit search end result that might trick the inattentive into clicking an advert after they solely wished data. What makes issues worse is that dangerous actors have discovered a number of methods to abuse these fake search outcomes to rip-off individuals.
A standard tactic for getting individuals to obtain and set up malware is to trick them into clicking a search advert disguised because the legit firm that makes the specified software program. Malwarebytes reviews that attackers now use Punycode in Google Adverts to make their URLs look much more genuine.
This tactic is named a “homograph assault” as a result of it makes use of Unicode characters of non-Latin scripts, like Cyrillic, Arabic, Greek, Chinese language, and others, to create a cloned URL that results in a rip-off web site. Malwarebytes factors to a lately found malicious Google advert for the KeePass password supervisor for example.
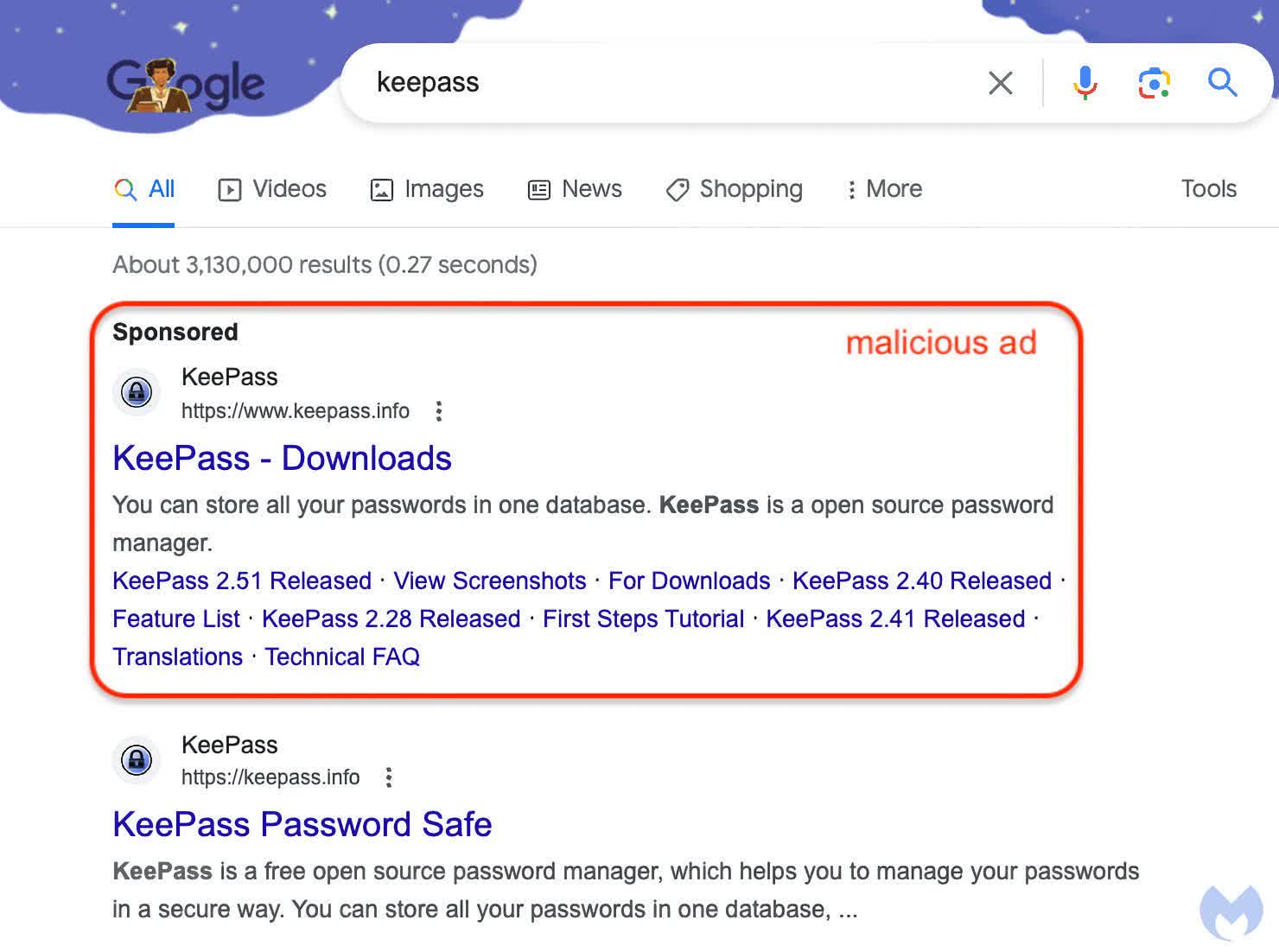
Beforehand, attackers would use subdomains and extensions much like the location they had been mimicking to trick customers into clicking, however these are fairly simple to identify. Nonetheless, by translating a URL into Punycode, dangerous actors can create an handle that appears fully genuine.
As you possibly can see within the picture above, the bogus URL appears equivalent to the genuine one beneath it. This trick is sneaky sufficient to idiot essentially the most attentive and tech-savvy customers. The one giveaway seems after clicking the bogus advert and going to the malicious web site. As soon as there, the browser’s handle bar will present the handle in Unicode, giving the ruse away. Sadly, except the person is aware of it could possibly be a rip-off, most will not even have a look at the handle bar, particularly when the web site that seems is almost equivalent to the software program firm’s.
Nonetheless, even wanting on the Unicode handle within the browser, customers may nonetheless miss the delicate visible cue if they don’t seem to be wanting rigorously. Discover within the picture beneath how the one distinction between the legit handle on the left and the bogus one on the suitable is the tiny image underneath the ‘ok.’ Customers may simply miss this signal or dismiss it as a speck on their monitor.
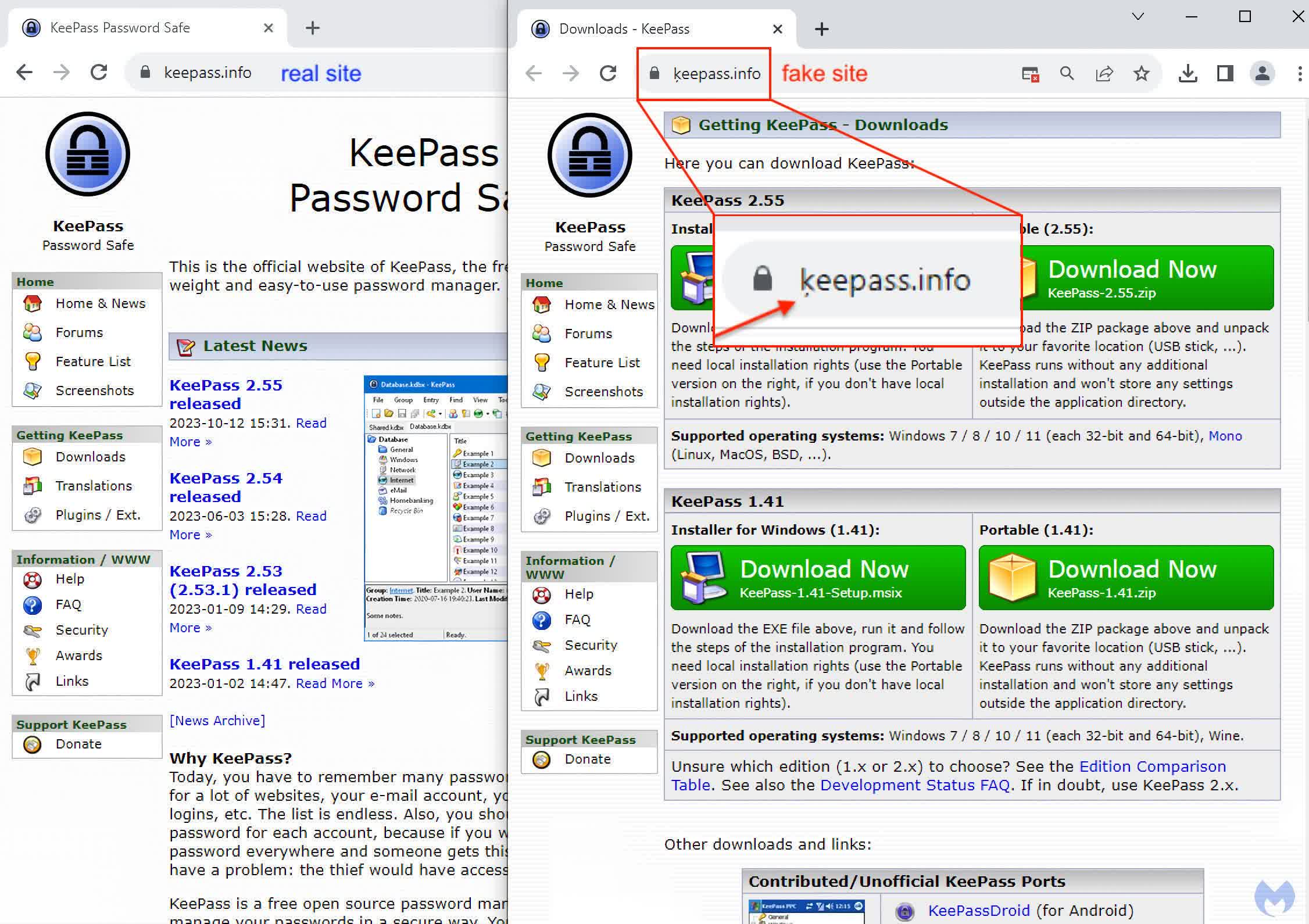
Homograph assaults have been round for some time, however that is the primary time Malwarebytes has seen it used along side Google adverts. Sadly, there isn’t any easy repair, particularly if attackers use different methods to make their faux websites appear actual.
Your finest guess is to keep away from clicking search end result adverts when searching for software program. It is best to go on to the corporate’s web site and search for the software program straight from the supply or use a trusted mirror like TechSpot Downloads. We authenticate all our downloads, scanning the software program regionally and thru VirusTotal to make sure they’re malware-free.
Backside line: Keep away from clicking adverts in Google search outcomes. We’ve got issued related warnings that they can not be trusted. At least, you’re handing Google your advert preferences so as to add to your current (and sure intensive) promoting profile. At worst, you possibly can land on an internet site which means to do you hurt. Till Google figures out a technique to stop dangerous actors from abusing its advert platform, there’s actually no legit motive to click on on their adverts.




