China-linked hackers suspected of exploiting zero-day flaw in software program utilized by ISPs

[ad_1]
Why it issues: A zero-day vulnerability that impacts ISPs and MSPs is a severe concern, because it may simply affect crucial infrastructure and nationwide safety if exploited on a bigger scale. Furthermore, the suspected involvement of Chinese language state-sponsored hacker teams like Volt Storm and Bronze Silhouette make the vulnerability notably alarming. The danger of widespread disruption underscores how prone our important providers are to cyberattacks.
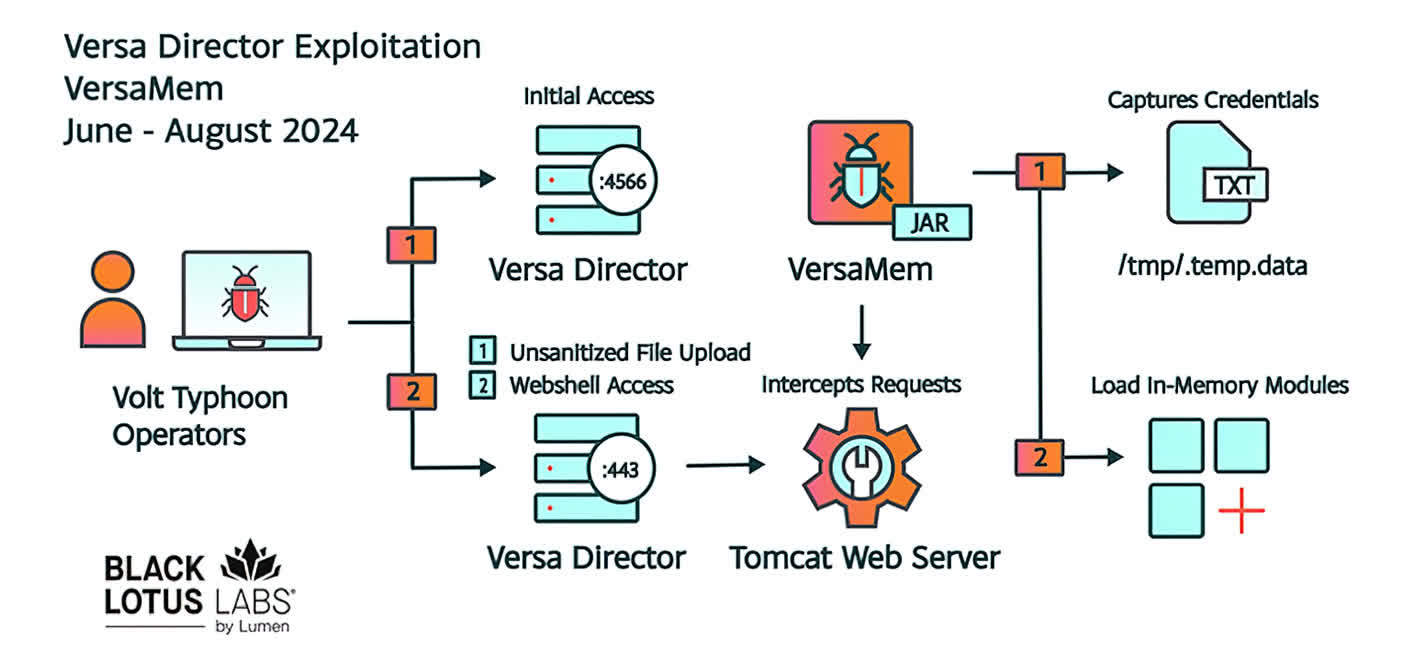
Black Lotus Labs has found a zero-day vulnerability in Versa Director servers, a virtualization platform broadly utilized by ISPs and managed service suppliers. This vulnerability, probably linked to Chinese language state-sponsored hacker teams, poses a major danger to those organizations.
Recognized as CVE-2024-39717, this crucial flaw was publicly introduced on August 22, 2024, and impacts all variations of Versa Director software program previous to model 22.1.4. The vulnerability is especially regarding for ISPs and MSPs, as they rely on Versa’s software-defined broad space community (SD-WAN) purposes to handle community configurations.
The vulnerability’s discovery has brought on alarm as a consequence of its potential to penetrate enterprise networks through Versa Director servers, that are liable for important community capabilities. Black Lotus Labs recognized a customized net shell, named “VersaMem,” that exploits this flaw to extract login credentials.
A notable characteristic of VersaMem is its modularity, which permits it to load further Java code straight into the server’s reminiscence, successfully evading detection.
International monitoring information from Black Lotus Labs reveals that the vulnerability has been exploited by means of compromised small-office/home-office gadgets in assaults concentrating on 4 victims in the USA and one overseas. These assaults, primarily affecting the ISP, MSP, and IT sectors, have been ongoing since June 12, 2024.
The attackers initially achieve entry by exploiting an uncovered administration port on the Versa Director, designed for connecting Director nodes for prime availability, which they then use to deploy the VersaMem net shell.
Black Lotus Labs suspects that Chinese language state-sponsored hacker teams, referred to as Volt Storm and Bronze Silhouette, are orchestrating the exploitation of this vulnerability. Their evaluation signifies that Volt Storm is actively concentrating on unpatched Versa Director methods.
The exploitation marketing campaign is taken into account extremely vital by Black Lotus Labs as a result of severity of the vulnerability, the sophistication of the risk actors, and the crucial position of Versa Director servers in community operations.
Organizations utilizing Versa Director are strongly suggested to improve to model 22.1.4 or later. Moreover, they need to overview safety advisories issued by Versa Networks on July 26, 2024, and August 8, 2024.
The severity of this vulnerability and the potential penalties of compromised Versa Director methods led Black Lotus Labs to publicly launch this info.
Lumen Applied sciences has additionally shared this crucial risk intelligence with related US authorities companies to alert them to the potential dangers to nationwide strategic belongings.
[ad_2]
Source