TP-Hyperlink Tapo sensible bulb vulnerabilities might expose Wi-Fi passwords to attackers

[ad_1]
Why it issues: You are in all probability accustomed to TP-Hyperlink’s Tapo sensible bulbs. They’re extremely fashionable, particularly on Amazon, and the companion app has over 10 million downloads on Google Play. However researchers have found 4 vulnerabilities in a selected mannequin of bulb and the Tapo app that might enable attackers to steal Wi-Fi passwords, amongst different issues.
As reported by Bleeping Computer, researchers from Universita di Catania and the College of London wrote in a paper that IoT merchandise have gotten more and more pervasive. As such, they wished to conduct a vulnerability evaluation and penetration testing session on the Tapo L530E, presently the best-selling sensible bulb on Amazon Italy.
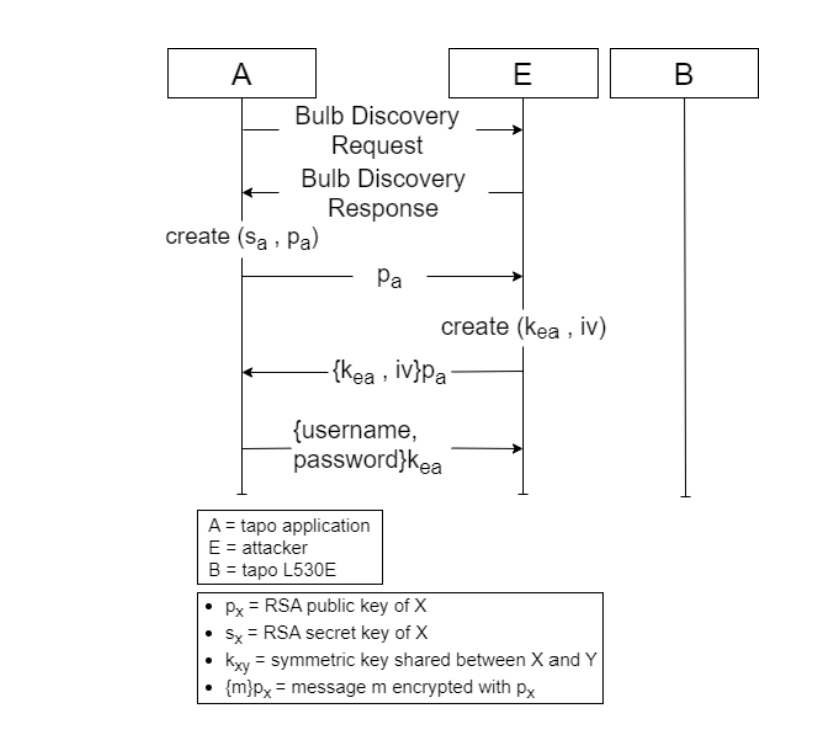
The outcomes weren’t good for TP-Hyperlink. Researchers discovered 4 vulnerabilities, the primary of which was calculated as having the best CVSS v3.1 vulnerability rating: 8.8, making it excessive severity. It is as a result of an absence of sensible bulb authentication with the Tapo app, permitting attackers to impersonate the bulb through the session key alternate step.
The vulnerability, current in all Tapo sensible units that use the TSKEP protocol, permits hackers to retrieve Tapo consumer passwords and manipulate Tapo units.
The second flaw can also be classed as excessive severity (7.6 rating) and stems from a hard-coded quick checksum shared secret. This lets an adjoining attacker acquire the key used for authentication through the Bulb Discovery part by way of a brute-force assault or by decompiling the Tapo app.
The third safety problem (4.6 rating) is an absence of randomness throughout symmetric encryption that allows an attacker to make the cryptographic scheme predictable.
The ultimate vulnerability (5.7 rating) pertains to inadequate message freshness, which retains session keys legitimate for twenty-four hours and permits attackers to replay messages throughout that interval.
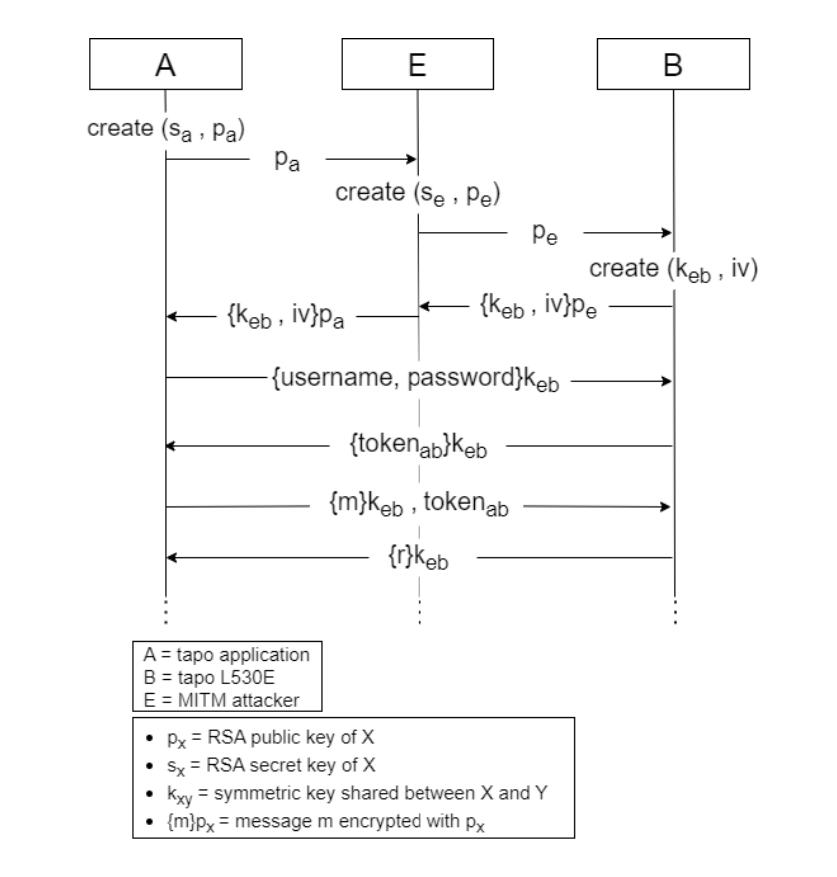
There are a number of eventualities during which somebody might exploit the vulnerabilities, probably the most critical being bulb impersonation and retrieval of Tapo consumer account particulars. This might enable an attacker entry to the Tapo app and, amongst different issues, steal a consumer’s Wi-Fi password. Whereas the system must be in setup mode for the assault to work, the attacker can repeatedly deauthenticate a bulb, forcing a consumer to run the setup once more.
The researchers additionally warned of Man-In-The-Center assaults with a configured and unconfigured Tapo L530E system, letting attackers intercept communications and retrieve Tapo passwords, SSIDs, and Wi-Fi passwords.
The excellent news is that the vulnerabilities have been reported to TP-Hyperlink by way of its Vulnerability Analysis Program (VRP). The corporate acknowledged all of them and mentioned it has began engaged on fixes each on the app and on the bulb firmware ranges. No phrase on when they are going to get right here past their launch “in the end.”
[ad_2]
Source